 |
Security
You cannot own a PC or laptop today without taking
adequate security measures. The Internet may have opened
up many opportunities, but it is also a dangerous place
for an unprotected PC.
In order to cover yourself, both online and offline, you
will need to follow some simple guidelines. It's
very important to understand that in security, one
simply cannot say "what's the best firewall?'' and be
done. There are two extremes: absolute security
and absolute access. The closest we can get to an
absolutely secure machine is one unplugged from the
network, power supply, locked in a safe, and thrown at
the bottom of the ocean. Unfortunately, it isn't
terribly useful in this state. A machine with absolute
access is extremely convenient to use: it's simply
there, and will do whatever you tell it, without
questions, authorization, passwords, or any other
mechanism. Unfortunately, this isn't terribly practical,
either.
You
must protect your network from outside attacks as well as protect each
PC from email and other vulnerabilities.
Triumphant Software can help with the policies and technologies to
provide the level of security you need.
Here
are some of our suggestions for security.
The Basics: Spotting and Eliminating Threats
As the saying goes, before you can run, you must learn
how to walk. And you can consider your first baby step
into computer security installing the basic software
needed to detect and eliminate threats.
-
Use a firewall
We recommend both a network firewall and a software
version for your PC. You can think of a
firewall as a sort of shell around your computer or
network that identifies and filters out threats,
while letting secure information pass through it and
reach your computer.
-
Install and update anti-virus software
Viruses, worms, Trojan horses and other forms of
malware can find their way onto your computer by
various means a firewall cannot detect, including
downloading malicious email attachments and files
from the internet. So to protect your PC you'll also
need strong regularly updated anti-virus software.
-
Install and run anti-spyware software
Even though firewalls and anti-virus programs are
more well-known when it comes to basic security
steps than installing anti-spyware software, it may
actually be your anti-spyware program that provides
your computer with the most significant increase in
security.
Next, Tweaking Settings and Making Usage Adjustments
There are a number of more specific weak points in your
computer's armor that need to be shored up either by
making some personal behavior adjustments to compensate
for the particular security weakness or by making the
necessary upgrades to minimize its vulnerability.
-
Strengthen your web browser security
-
Install the latest OS service pack
-
Select secure software and update it regularly
-
Disable file sharing on your hard drives
-
Be cautious when downloading
Safely Emailing
-
Use a first-rate email client
-
Handle email attachments carefully
-
Do not click on email links haphazardly
-
Set up email filters
Protecting Your Password
You would never consider setting the combination of your
family safe to something as simple as, "1 … 2 … 3." But
even though computer and Internet passwords provide
access to far more money than your home safe, many
people set themselves up to get hacked when they select
passwords that are far too simple or that are changed
too infrequently.
-
Keep hackers guessing
-
Use a variety of different passwords
-
Password protect your computer login access
Wireless Protection
-
Protect your wireless network
-
Do not use a neighbor's WiFi connection
At Triumphant
Software, we
will manage your routers, firewalls, and wireless access
devices to ensure:
-
The
device is running the current OS or firmware
-
The
device is configured securely
-
Perform
any Add/Move/Change to the configuration
-
Monitor
the device to make sure it is up and running
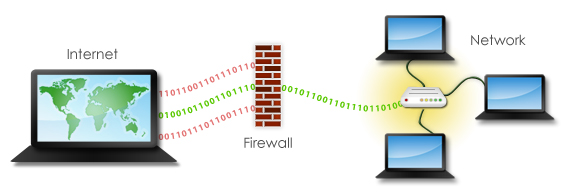 Firewalls are a critical first line of
defense against Internet security threats. Know your
firewall is up and actively protecting your network.
Our service includes proactive management, problem
remediation, ongoing configuration consultation and
changes.
If your company has routers connecting
multiple locations together or you have one large
location that has multiple networks, you know the
importance of keeping your routers up and running. With
our Maintenance Plan, you can ensure that your routers
will be kept current with the latest OS updates and that
they are properly configured for optimal performance.
Disaster Recovery / Business Continuity
Disaster recovery and
business continuity planning are processes that help
organizations prepare for disruptive events—whether an
event might be a hurricane or simply a power outage
caused by a backhoe in the parking lot. Organizations
should have a plan in place (usually referred to as a
"Disaster Recovery Plan", or "Business Continuity Plan")
that outlines how this will be accomplished. The key to
successful disaster recovery is to have a plan
(emergency plan, disaster recovery plan, continuity
plan) well before disaster ever strikes. At
Triumphant Software, we can assist with everything from
assisting with existing security needs and configuring a
backup plan to formulating a
Disaster Recovery Plan for true business continuity.
Find out more...
Firewalls are a critical first line of
defense against Internet security threats. Know your
firewall is up and actively protecting your network.
Our service includes proactive management, problem
remediation, ongoing configuration consultation and
changes.
If your company has routers connecting
multiple locations together or you have one large
location that has multiple networks, you know the
importance of keeping your routers up and running. With
our Maintenance Plan, you can ensure that your routers
will be kept current with the latest OS updates and that
they are properly configured for optimal performance.
Disaster Recovery / Business Continuity
Disaster recovery and
business continuity planning are processes that help
organizations prepare for disruptive events—whether an
event might be a hurricane or simply a power outage
caused by a backhoe in the parking lot. Organizations
should have a plan in place (usually referred to as a
"Disaster Recovery Plan", or "Business Continuity Plan")
that outlines how this will be accomplished. The key to
successful disaster recovery is to have a plan
(emergency plan, disaster recovery plan, continuity
plan) well before disaster ever strikes. At
Triumphant Software, we can assist with everything from
assisting with existing security needs and configuring a
backup plan to formulating a
Disaster Recovery Plan for true business continuity.
Find out more...
|
 |

 Firewalls are a critical first line of
defense against Internet security threats. Know your
firewall is up and actively protecting your network.
Our service includes proactive management, problem
remediation, ongoing configuration consultation and
changes.
If your company has routers connecting
multiple locations together or you have one large
location that has multiple networks, you know the
importance of keeping your routers up and running. With
our Maintenance Plan, you can ensure that your routers
will be kept current with the latest OS updates and that
they are properly configured for optimal performance.
Disaster Recovery / Business Continuity
Disaster recovery and
business continuity planning are processes that help
organizations prepare for disruptive events—whether an
event might be a hurricane or simply a power outage
caused by a backhoe in the parking lot. Organizations
should have a plan in place (usually referred to as a
"Disaster Recovery Plan", or "Business Continuity Plan")
that outlines how this will be accomplished. The key to
successful disaster recovery is to have a plan
(emergency plan, disaster recovery plan, continuity
plan) well before disaster ever strikes. At
Triumphant Software, we can assist with everything from
assisting with existing security needs and configuring a
backup plan to formulating a
Disaster Recovery Plan for true business continuity.
Find out more...
Firewalls are a critical first line of
defense against Internet security threats. Know your
firewall is up and actively protecting your network.
Our service includes proactive management, problem
remediation, ongoing configuration consultation and
changes.
If your company has routers connecting
multiple locations together or you have one large
location that has multiple networks, you know the
importance of keeping your routers up and running. With
our Maintenance Plan, you can ensure that your routers
will be kept current with the latest OS updates and that
they are properly configured for optimal performance.
Disaster Recovery / Business Continuity
Disaster recovery and
business continuity planning are processes that help
organizations prepare for disruptive events—whether an
event might be a hurricane or simply a power outage
caused by a backhoe in the parking lot. Organizations
should have a plan in place (usually referred to as a
"Disaster Recovery Plan", or "Business Continuity Plan")
that outlines how this will be accomplished. The key to
successful disaster recovery is to have a plan
(emergency plan, disaster recovery plan, continuity
plan) well before disaster ever strikes. At
Triumphant Software, we can assist with everything from
assisting with existing security needs and configuring a
backup plan to formulating a
Disaster Recovery Plan for true business continuity.
Find out more...